- Several password managers are subject to a new attack
- The attack abuses opacity parameters and automatic capacities
- Passwords, 2FA codes and credit card details can be stolen
During the recent Conference DEF Con 33, independent researcher Marek Tóth unveiled a jacking attack which he claims could exploit the automatic capacities of six of the largest password managers.
The attack is capable of stealing passwords, 2FA codes and credit card details, making it serious concern for the tens of millions of users of the password manager.
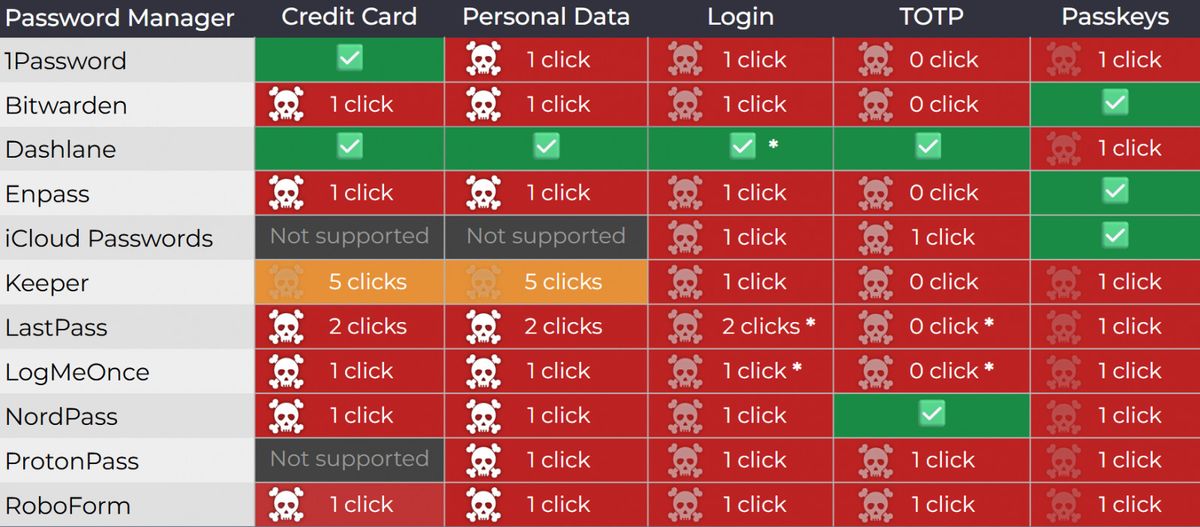
Tóth tested the attack on the versions of 1Password, Bitwarden, Enpass, iCloud passwords, Lastpass and Logmeonce, and found that browser -based variants could flee data stored under the right conditions.
Major managers of risk passwords
The attack is based on the use of a website that uses opacity parameters, overlays or a pointer event to make the automatic function of the web -based password manager to appear invisible. Website can be malicious sites, or legitimate sites that have been compromised.
The attacker then uses a contextual window or CAPTCHA which deliberately places the user clicks on the controls of the hidden password manager, automatically identification information in the form and steal it.
What makes this attack vector even more worrying is that the attacker can use a universal attack script to identify the active password manager on the web browser and adjust the attack to target it specifically.
Other variations in the attack have been demonstrated at DEF Con 33, including several subtypes based on DOM which abuse from opacity to the element, the parent element, the root and the superposition level, as well as an attack which can trigger the automatic wherever the cursor is placed.
Tóth informed the companies on which he tested the attack vector in April 2025, also declaring that public disclosure would be made to the DEF Con 33 in August. Socket cybersecurity researchers checked Tóth’s methods and helped notify affected password managers.
Several password managers remain vulnerable to the attack, including these versions:
- 1PASSWORD 8.11.4.27
- Bitwarden 2025.7.0
- ENPASS 6.11.6 (partial correction implemented in 6.11.4.2)
- ICloud 3.1.25 passwords
- Lastpass 4,146.3
- Logmeonce 7.12.4
The latest versions of Dashlane, Nordpass, Protonpass, RoboForm and Keeper were all corrected against the demonstrated attack vector of Tóth. Lastpass and Logmeonce are currently working on the attacks for the attack.
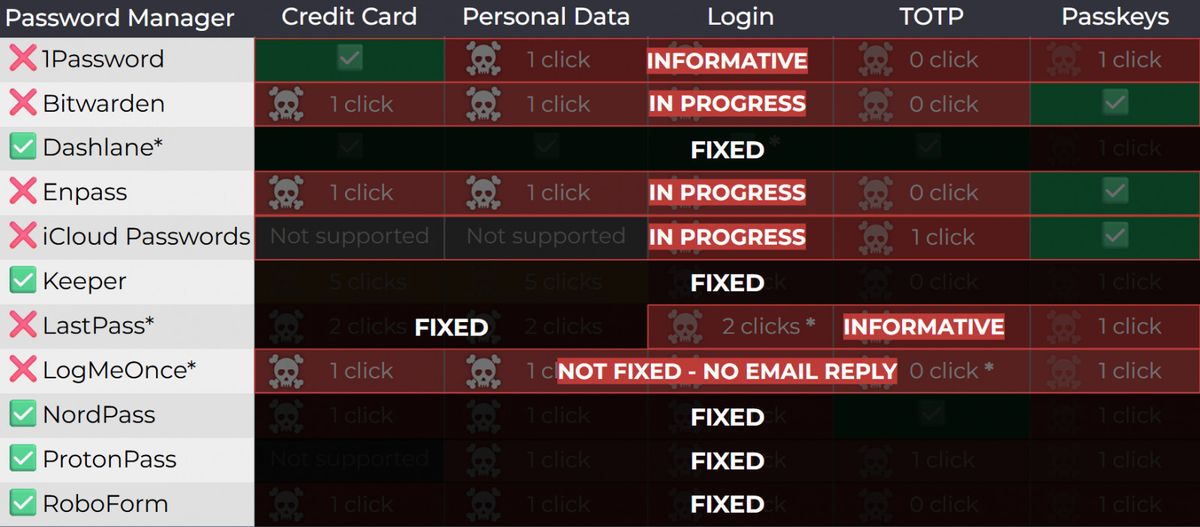
Several companies have published comments to Bleeping Compompute After the publication article.
Lastpass:
“We appreciate the work of security researchers, like Marek Tóth, which helps to raise awareness of potential threats and to improve industry safety. The vulnerability of Jacking to discovery of Marek highlights a wider challenge faced by all password managers: finding the right balance between user experience and convenience, while addressing the evolution of threat models.
Lastpass has implemented certain click jacking guarantees, including a contextual notification that appears before credit cards and personal automatic filling details on all sites, and we are committed to exploring ways to protect users more while continuing to preserve the experience that our customers expect.
In the meantime, our intelligence, attenuation and climbing team (time) threats encourages all users of password managers to remain vigilant, to avoid interacting with suspicious overlays or pop-ups and to keep their last-up-up extensions. “- Alex Cox, director of the threat, attenuation, climbing (time) at the last stage.
1Password:
“Clickjacking is not unique to expanding the 1PASSWORD browser. This is a long-standing web attack technique that largely affects websites and browser extensions. Because the underlying problem lies in how browsers make web pages, we believe that there is no complete technical correction that navigators extensions can provide their own.
We take this seriously and all security concerns, and our approach to this particular risk is to focus on giving customers more control. 1PASSWORD already requires confirmation before updating payment information, and in our next version, we extend this protection so that users can choose to activate confirmation alerts for other types of data. This helps users to remain informed in the event of automatic and control of their data. “- Jacob Deprisest, ciso at 1Password.




