- Launched on July 27, 2025, a new VPN service seeks to solve problems with the confidence of suppliers
- VP.NET uses Intel SGX material to offer supposedly “cryptographically verifiable confidentiality”
- Researchers have discovered certain vulnerabilities with Intel SGX systems in the past
A new VPN service has just landed on the market, promising to adopt a completely different technical approach to user confidentiality.
Abbreviation of verified confidentiality, vp.net claims to be built in a way that physically separates the identities of users from their navigation activity at the material level. In doing so, the supplier seeks to solve problems related to the confidence of virtual private network suppliers (VPN). So, forget VPN’s policies without log and welcome “cryptographically verifiable confidentiality”.
The supplier launched the application on June 27, 2025, on all the main platforms, namely Windows, MacOS, Linux, Android and iOS, and now strives to become the VPN of the future. However, not without controversy.
The problem with software without software
All the best VPN services are currently providing strict non-lobarithm policies. These guarantee that the supplier never stores any of your identifiable data and is regularly checked with independent non-logrithms audits.
The problem is that even the third -party VPN audits require a dose of trust.
“An audit only proves that something was true at that time. This is why we bring back mathematical and verifiable cryptography in the mixture so that when we say private, you are in fact private,” the founders of VP.NET, Andrew Lee told Techradar.
Founder of Private Internet Access (PIA), an VPN supplier of popular non-lugarithm, Lee later achieved that many users now need a level of confidentiality that is not based on trust. He then joined other confidentiality developers to build a new type of VPN service.
That said, it should be noted that PIA is one of the companies that have proven their complaints without log in real life over the years, which did not do it but twice in court. Another example is Mullvad, who left a police raid empty hands in Sweden in 2023.
What VP.NET does differently
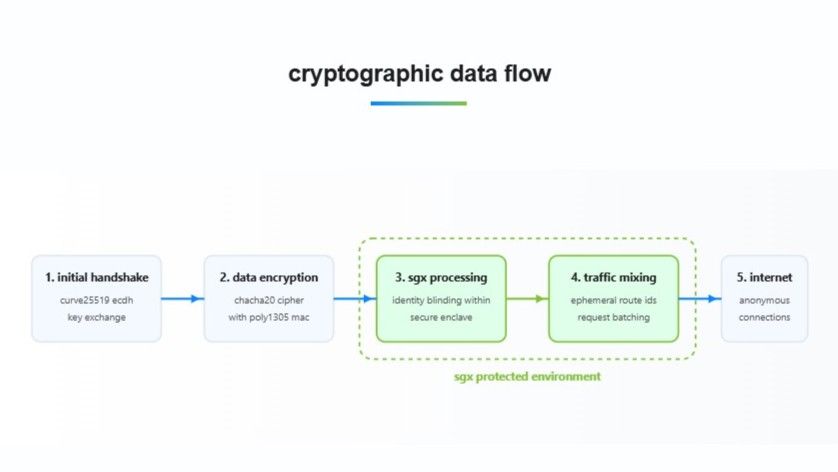
The big novelty with vp.net lies in its technology. The company uses Intel SGX equipment, which promises to provide “cryptographically verifiable confidentiality”.
For the less technical, all you should know is that all sensitive operations, those that could somehow reveal your identity, occur in so -called encrypted enclaves. These are secure and isolated spaces in the software infrastructure which physically prevent the VPN supplier from accessing the activities that occur inside.
In other words, this mechanism should make “technically impossible to associate your identity with what you do online,” explains the supplier.
Not only encryption, however; The system also claims to use the SGX certificate. It is a safety mechanism which ensures that the encrypted enclaves work as they should, preventing the supplier or any other third party from accessing the activities that occur inside. This is “verifiable by customers using Intel certificate services,” said the supplier. You can see all the technical details of VP.NET here.
Above all, VP.NET also offers a certain protection against metadata monitoring, which means all the details that are not the content. Echoing that the innovative NYMVPN network and the DAITA tool in Mullvad is, VP.NET also uses certain techniques to prevent traffic analysis and obscure real use models.
Beyond the new infrastructure, VP.NET also includes all the conventional features that you expect from a VPN.
These include support for secure and fast protocol Wire Guélectricity, alongside security features as a killing switch and DNS leakage protection. The addition of post-quantum encryption support is also in progress.
All applications are also fully open-source, so that anyone with technical knowledge can check the code to see if the software behaves as it should. You can take a look at the supplier’s public standards by heading to the VP.NET GIFTHUB page.
Is it really the ball test?
Despite the right premises on paper, Intel SGX Tech is certainly not without defects.
In 2019, for example, a team of researchers discovered a way to execute and hide malware on Intel systems. Worse, this malicious software was undetectable by antivirus tools at the time.
This can be among the reasons why Intel has corrected several safety holes in 2023, addressing many existing defects and vulnerabilities.
Such a security correction certainly did not convince everyone in the industry, including the CEO of NYMVPN, which is another VPN supplier seeking to question the problems with the confidence of VPN suppliers. “I prefer decentralization and advanced cryptography rather than believing that Intel has produced a silver ball,” said Harry Halpin, CEO of NYMVPN, in Techradar.
Another litigious point is behind the vp.net team. Well -known names in the world of Bitcoin, Roger Ver and Mark Karpelès have had legal problems in the past.
Commenting on this last point, Karpelès told Techradar: “for the The way we build the system, there is no need to trust the team behind VP.NET. We provide independent systems that have checked by itself, such as a connection if everything is certain. So, even if I wanted to connect or do something like that, there is no way to do anything. “”




