- Apple may have resolved mercenary Spynerains software attacks
- The so-called application of memory integrity (MIE) is ready to make spy software attacks more difficult to develop and maintain
- The new iPhone 17 and iPhone Air series are also the first to include an improved memory marking extension (EMTE) to offer even more security
Apple may have found a solution against attacks by sellers of mercenary spy software.
The great technology giant says that its new memory memory application (MIE) should make spy attacks much more difficult to develop and maintain.
The application of memory memory (MIE) will be available for all up -to -date iPhone users to the new iOS 26. However, anyone obtaining an iPhone 17 series or an iPhone air will also benefit from the new improved memory extension functionality (EMTE).
Built on the original ARM memory marking extension (MTE) published in 2019 – a tool for detecting and prevention of bugs in memory in terms of software – EMTE now acts as a real -time defense for iPhone users.
With iPhone products already well equipped against attacks based on malware, these new protections will considerably increase user security – in a way that even the best VPN or other safety tools could not.
“Due to the way in which he considerably reduces the ability of an attacker to exploit the vulnerabilities of memory corruption on our devices, we believe that the application of the integrity of memory represents the most important upgrade to memory security in the history of consumer operating systems”, reads Apple’s official announcement.
Problems with spy software and memory security
As Apple explains Apple in its blog article, attacks on mercenary Spymetrical software are more complex and invasive than phishing, malware and other current consumer attacks. Above all, spy software attacks are the only attacks on the system against iOS systems observed in the wild, according to the supplier.
“The known Spymetric Software Chains used against iOS share a common denominator with those that target windows and Android: they exploit the vulnerabilities of memory security, which are interchangeable, powerful and exist throughout the industry,” explains Apple.
Improvement of memory security has been a major objective for the Apple security team from at least 2018. Advanced fast until September 9, 2025, The Big Tech Giant published a complete defense of memory security called Memory Integrity Enforcement (MIE) – A system built on the secure technology of Apple memory beneficiaries.
On the latest iPhone, MIE is also associated with an improved memory marking extension (EMTE) in synchronous mode. This means that the functionality checks the corruption of memory in real time.
How to apply the new integrity of Apple memory (MIE) can repair them
“With the introduction of the iPhone 17 range and the iPhone Air, we are delighted to provide the application of the integrity of memory: the very first complete protection and always on the protection of memory covering the attack surfaces – including the core and more than 70 user processes – built on the improved extension of memory marking (EMTE) and the secure typical beneficiaries and of tag, “indicates the announcement of the Apple.
More specifically, the EMTE function targets two of the most common memory corruption bugs: buffer overflows and unrelated use.
For the least technical people, all you need to know is that the two vulnerabilities allow attackers to read or even corrupt the memory to which they should not have access.
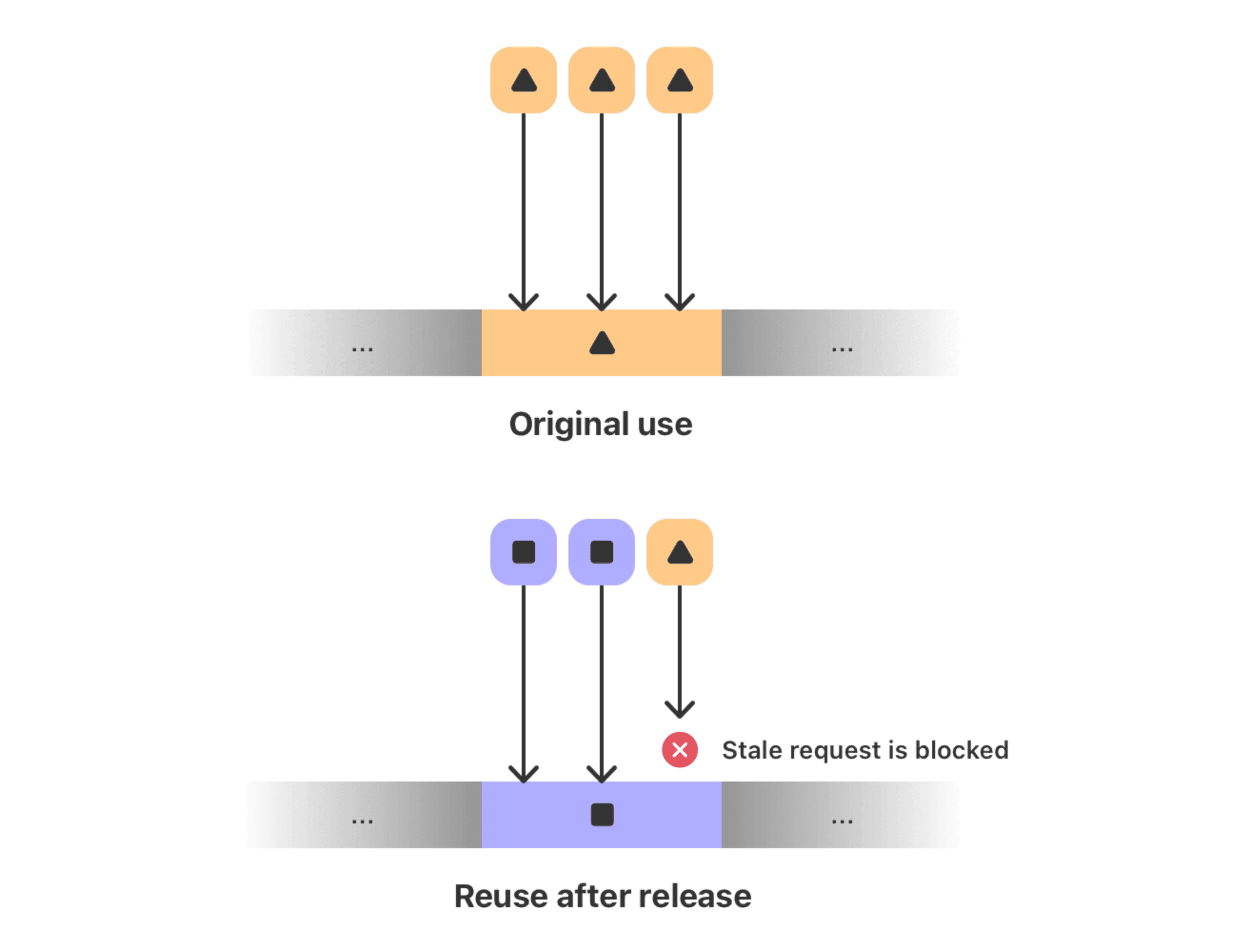
So far, at least. According to Apple’s security team, the iPhone is now the first smartphone capable of preventing attackers from exploiting these bugs, making attacks much more expensive and unreliable to make. An attenuation that the team expects to work, for the very first time, against the well -known vulnerability Specter V1.
Without going into too many technical details, the additional protection provided by the new Apple MIE system means that, even if the attackers manage to exploit the corruption bug of an iPhone, the memory they could access or modify is extremely limited around this specific vulnerability.
For more information on operation, see the Apple blog.
Overall, “although there is no perfect security, MIE is designed to considerably limit attackers and their degrees of freedom during exploitation,” explains Apple.
In addition, not only Apple improves security in iPhone hardware and software, but the supplier also makes its EMTE function accessible to the public for all XCODE developers. In doing so, the team hopes that this will inspire a broader adoption in industry.




