- Fake Microsoft alerts cause users to make costly, panic-induced mistakes
- Visual authenticity no longer guarantees security in a manipulated digital landscape
- Cyberattacks increasingly target human psychology rather than technical weaknesses
The authority and familiarity of a big brand like Microsoft often offers users a sense of assurance – but new research has warned that this is not always the case.
Findings from the Cofense Phishing Defense Center assert that this trust can be exploited, as shown by a recent campaign in which criminals manipulated the Microsoft brand to deceive victims.
What appears to be a legitimate support process often becomes a gateway to financial and data compromise, bypassing conventional cybersecurity defenses.
How Financial Lures Trigger Deception
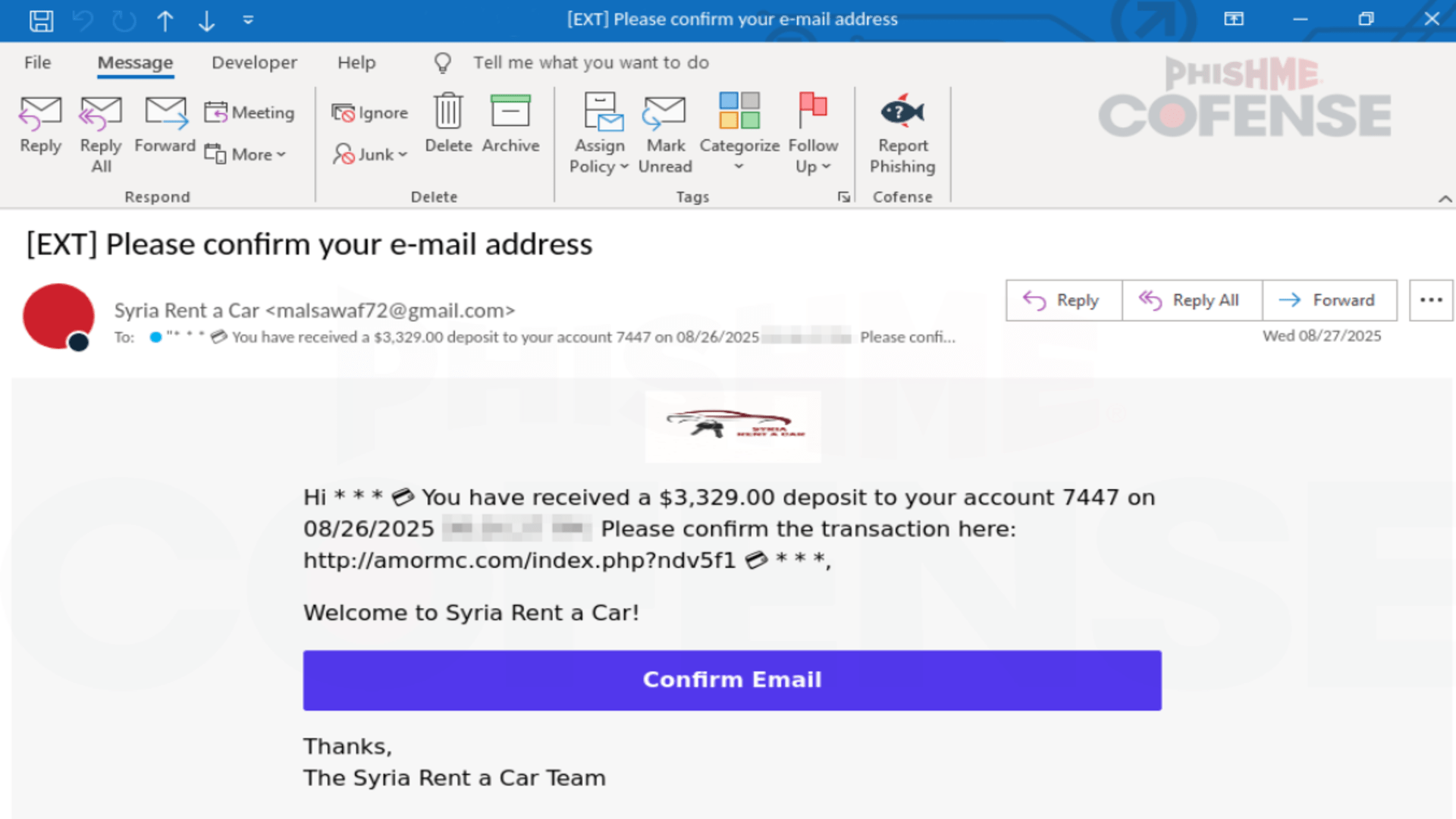
Cofense explains how the scam begins with an email that appears to come from a legitimate business, such as a car rental company, claiming that a refund is pending confirmation.
This “payment lure” is designed to appeal to human curiosity and the expectation of financial benefits.
When the recipient clicks to verify the email, they are redirected to a fake CAPTCHA page.
The goal of this step is not only to make the process seem authentic, but also to engage the user in a way that evades automated analysis tools.
By establishing early trust and commitment, criminals set the stage for a more manipulative encounter.
The real manipulation takes place on the next page, which hijacks the user’s browser with a fabricated Microsoft interface.
The browser appears locked and a series of pop-ups declare that the system has been compromised.
At the same time, the victim’s mouse becomes unresponsive, reinforcing the illusion of a system lock.
This tactic mirrors the visual and behavioral patterns of ransomware, generating fear and confusion.
The feeling of helplessness is intentional, pushing users to seek immediate solutions – and in this artificially induced crisis, a toll-free number for “Microsoft Support” is prominently displayed.
This seems to bring relief, but it actually leads directly to the perpetrators.
Once the victim calls the number, they are connected to a fraudster posing as a Microsoft technician, who may ask for credentials or persuade the victim to install remote access software.
Once control is gained, the criminal can steal data, transfer money, or install hidden malware.
Mitigating these scams requires both technical and behavioral defenses.
Organizations should combine the use of secure messaging practices with filtering, secure browsing controls and timely reporting processes to limit exposure.
Regular phishing simulations and awareness training help users quickly identify deceptions and respond safely.
If a system appears locked or displays alarming pop-ups, users should avoid interacting with on-screen phone numbers and instead contact the provider through verified channels.
Users should view even a well-known brand as an indicator of potential risk rather than a sign of legitimacy.
Visual authenticity should never be accepted as proof of safety, especially when associated with emergency or fear-based messages.
Follow TechRadar on Google News And add us as your favorite source to get our news, reviews and expert opinions in your feeds. Make sure to click the Follow button!
And of course you can too follow TechRadar on TikTok for news, reviews, unboxings in video form and receive regular updates from us on WhatsApp Also.